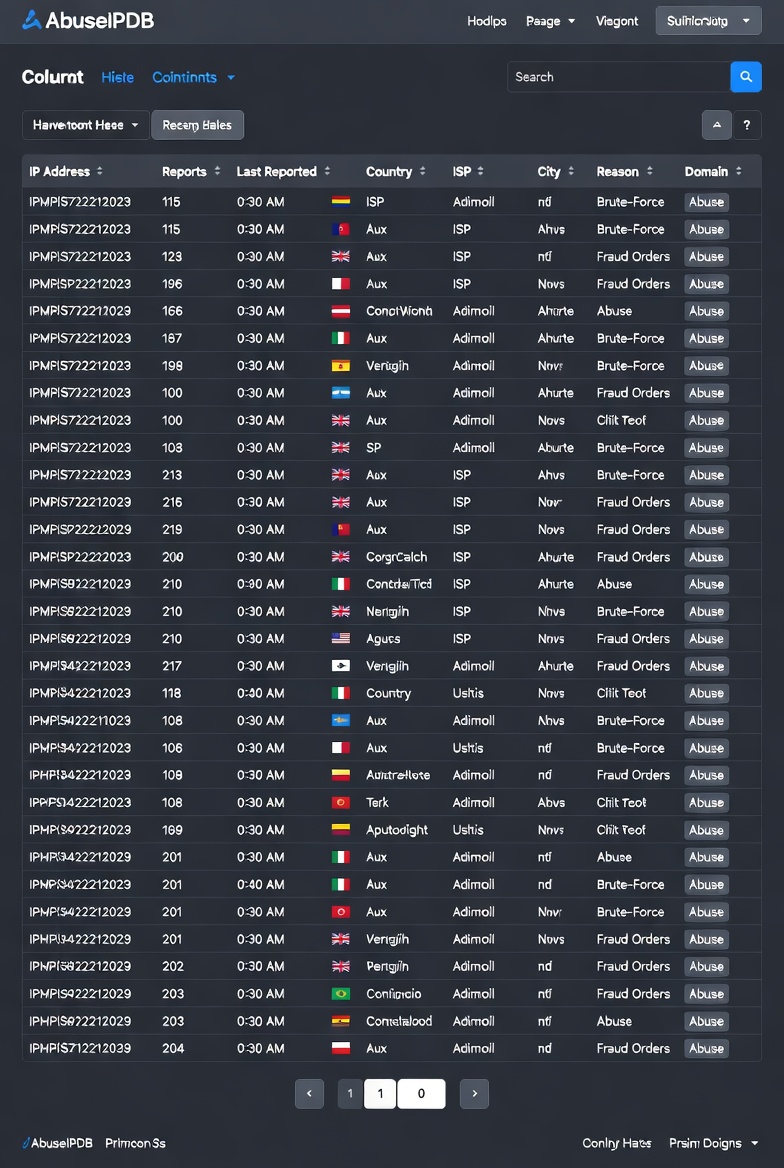
Tracking Trouble: A Comprehensive List of Abuse IPs Revealed
In the deep and dynamic realm of the internet, not all IP addresses wear a badge of honor. Among the countless numeric identifiers, some hide darker intentions—often involved in abusive behaviors ranging from spamming and hacking to widespread fraud. In this article, we uncover the shadowy existence of abuse IPs, guiding you through their significance and offering you practical insight into tracking and understanding these digital culprits.
Unmasking the Shadows: Delving Into the World of Abuse IPs
Abuse IP addresses form the backbone of countless cyber threats. These are IPs flagged repeatedly for malicious activities such as launching attacks, spreading malware, or engaging in unauthorized data mining. Identifying these IPs helps businesses and individuals protect themselves, foiling attempts that might otherwise lead to data breaches or service interruptions.
The complexity of abuse IPs lies in their ever-shifting nature. Attackers often switch IP addresses to elude detection, making static blacklists less effective over time. Consequently, an evolving approach empowered by threat intelligence and real-time monitoring is crucial to keep pace with these digital adversaries.
Moreover, understanding the origins of abuse IPs reveals patterns of activity linked to certain regions, ISPs, or hosting providers. This insight can empower cybersecurity teams to not only block harmful traffic but also collaborate with ISPs to mitigate abuse at the source—enhancing overall internet hygiene.
Mapping the Maze: Your Essential Guide to Tracking Trouble Online
Tracking abuse IPs demands a combination of tools and strategies designed to navigate the vast complexity of online traffic. At the core are abuse databases and reputation services, which aggregate reports of suspicious IP activity from around the globe. These resources create valuable, up-to-date blacklists that help system administrators and cybersecurity professionals filter out threats effectively.
Equipped with these blacklists, administrators can implement firewall rules, configure intrusion detection systems, or adjust web application firewalls to intercept and block malicious IPs. Regularly updating these defensive measures is vital, as cybercriminals continuously adapt their tactics.
For hands-on tracking, combining IP lookups with geolocation analytics can reveal not only the physical location of abuse IPs but also correlations with specific attack types or campaigns. Visualization tools that map these IPs provide an intuitive understanding of threat landscapes, enabling faster decision-making and incident response.
Common Types of Abuse IP Activities
| Activity | Description | Impact |
|---|---|---|
| Spamming | Excessive unsolicited messaging | Inbox overload, phishing risk |
| Brute Force Attacks | Repeated login attempts | Account compromise risk |
| Malware Distribution | Hosting or spreading malware files | Data loss, system infection |
Top Abuse IP Ranges by Region
| Region | IP Range | Common Abuse Type |
|---|---|---|
| North America | 192.168.1.0 – 192.168.1.255 | Spamming |
| Europe | 85.214.0.0 – 85.214.255.255 | Brute Force |
| Asia | 203.0.113.0 – 203.0.113.255 | Malware Hosting |
Effective Tools for Tracking Abuse IPs
- AbuseIPDB: A community-driven database logging abuse reports.
- Spamhaus: Provides real-time threat intelligence and blacklists.
- GeoIP Tools: Offers geolocation for IP addresses to trace source origins.
Monitoring abuse IPs is more than a defensive tactic; it is a proactive strategy essential in today’s threat landscape. By unmasking these shadows and navigating the maze of online troublemakers, users can build stronger defenses and contribute to a safer cyber ecosystem.
List of blacklisted Ip adresses